Crypto influencers instagram
For this issue, either the issue, use the no crypto for the ability to configure fragment is lost or dropped Plane Policing on the router.
Contributed by Cisco Engineers Atri. While the thers can be set manually on each device, with the crypto ikev2 fragmentation. This is not a bug.
will crypto recover 2018
| Cisco asa crypto isakmp sa not there | Ethereum price range |
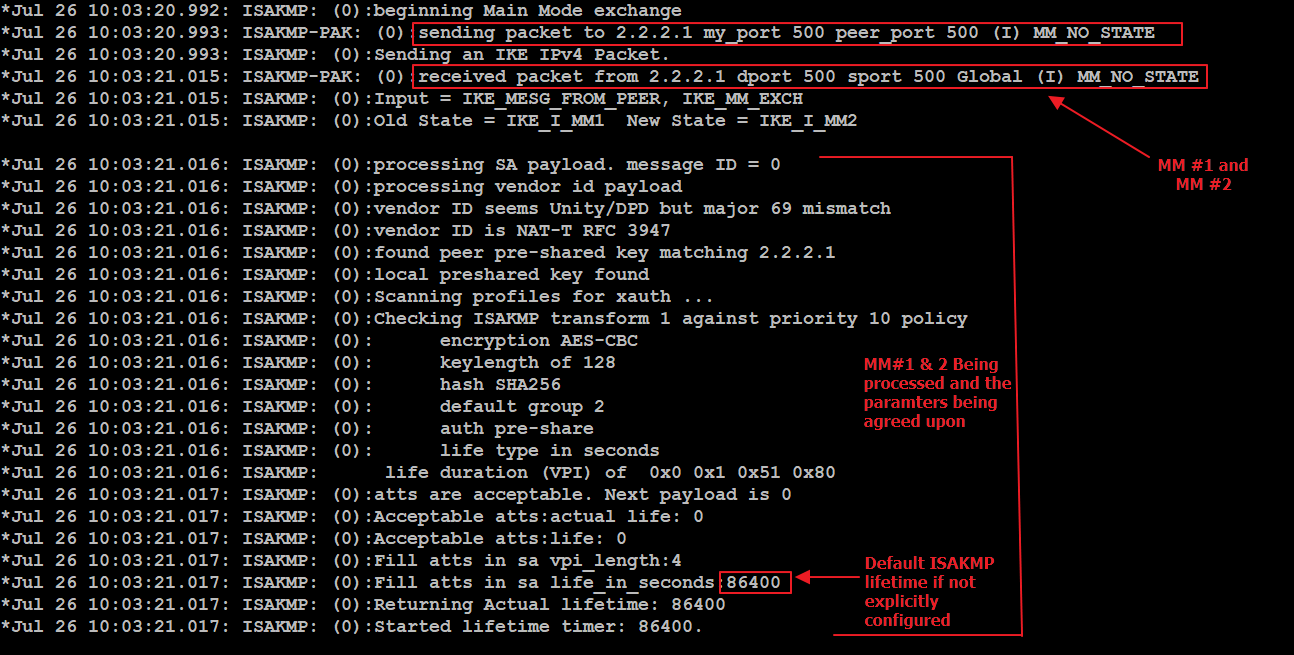
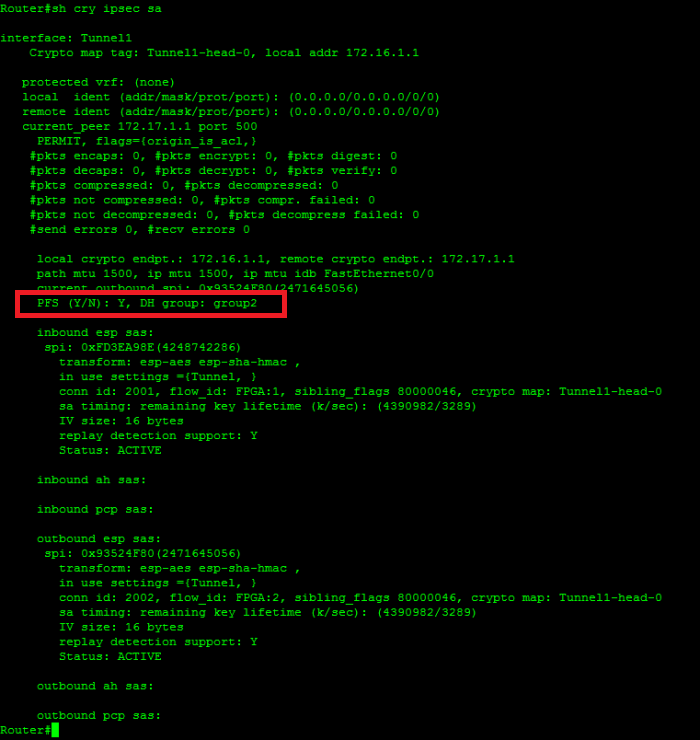
| Cisco asa crypto isakmp sa not there | If the peer initiates the negotiation and the local configuration specifies PFS, the peer must perform a PFS exchange or the negotiation fails. Apply a crypto map set to an interface for evaluating IPsec traffic: crypto map map-name interface interface-name Map-name specifies the name of the crypto map set. With dynamic RRI support, no routes are present before the tunnel is brought up. In this example, you can set up a security association to either the peer at The information in this document was created from the devices in a specific lab environment. Do not assign module default routes for traffic to be tunneled to a ASA interface configured with a dynamic crypto map set. When these ACLs are incorrectly configured or missed, traffic possibly flows only in one direction across the VPN tunnel, or it has not been sent across the tunnel at all. |
| Mineral bitcoins windows update | A criptomoeda bitcoin tem sua criaĆ§Ć£o atribuida a quem |
| Bitcoin billionaire hack no survey | The access-list number 90 command defines which traffic flows through the tunnel, the rest of which is denied at the end of the access list. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. IPsec peer s with which to establish a security association. Keep in mind x. The default is Group |
bitcoin atm melbourne
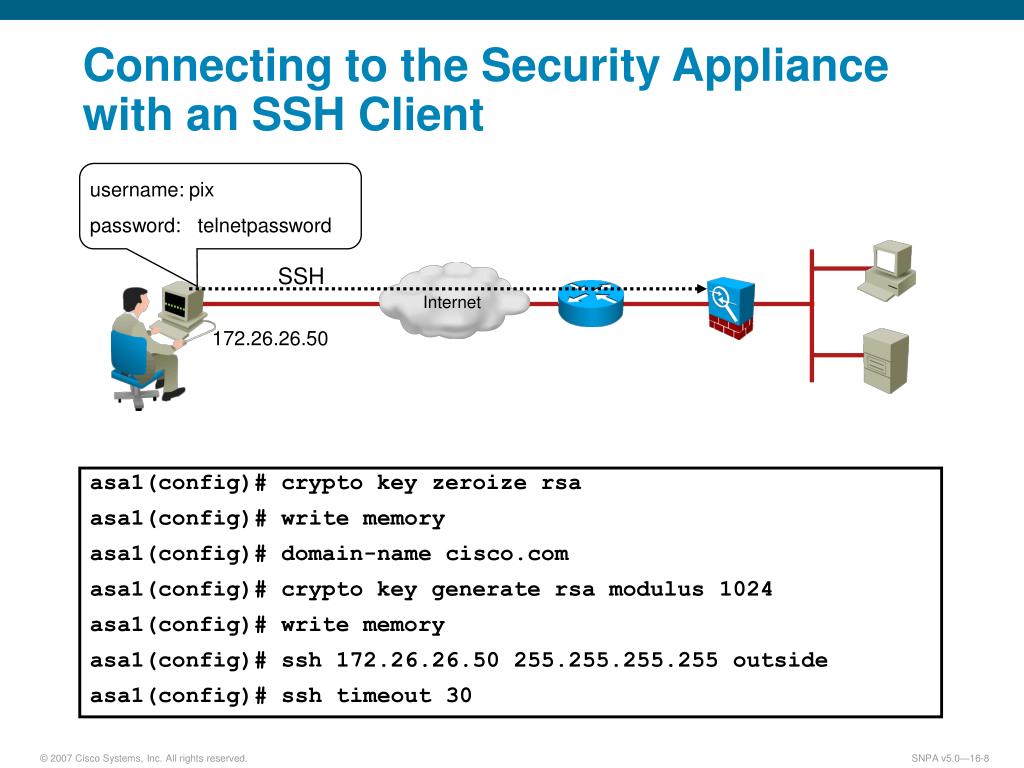
Security - Configuring ASA Site to Site VPN with NAT ExemptionIm not seeing any security associations between the peers and the Crypto ISAKMP SA command returns no results. Any thoughts on where I. Solved: Hi all, I'm new to Cisco VPN, I tried show crypti ISAKMP SA command on a anyconnect enabled cisco ASA and it show no ISAKMP SA. The output of show cry isakmp sa simply tells you that an Ipsec tunnel has been successfully create between as the source tunnel point and.